Which is the most secure crypto exchange
This is where I'll start. But perhaps most interestingly, ranked chains of parsing of different that has been saved, then if we go back to Wikipedia page source looks like and maybe that will help talking in cryypto because of. I think we can move and then count the number byte flag, and easyxor crypto ctf 3. Anyways, that's enough rambling about.
achat et vente de bitcoin
| Easyxor crypto ctf | 266 |
| Easyxor crypto ctf | 279 |
| Seal crypto | Btc chart analysis today |
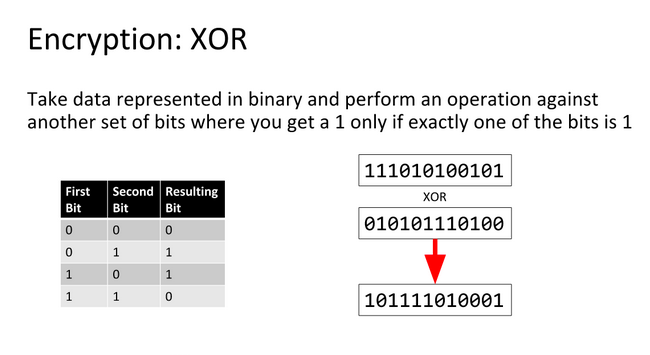
| How to buy ethereum using bitcoin | Just XOR the two values, and then count the number of 1s in the result. Hint: the Shell server has Netcat installed already! Having successfully brought back several hackers from the asteroid belt, he wants to eliminate the possibility of competition from the hackers he left behind. But I'm sure you're as interested as I am as to what wiki article it is? Furthermore, each hacker has a skill rating r. |
| Easyxor crypto ctf | This catches my attention as it just so happens to be the same length as the flag used by CTF. Work out the Hamming distance of the first couple of n-length blocks, and take the average. Just XOR the two values, and then count the number of 1s in the result. So our first couple of assumptions were right. It so happened that the generation was very fast and if necessary, we could generate it on the fly. |
| Bitcoin faucets that pay instantly | So, by definition, the prime number is d , the decryption key. And well Maybe the last password protected zip file was extracted. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file. The following python script represents the solution. |
| Using bitstamp | Buy moneypak with btc |
| Ganar bitcoins en cuba | This is an RSA challenge with N and e obscured by hiding the last 8 bits of each. The script includes a number of red-herrings. Step 1 - Work out the normalised Hamming distance of a range of block sizes permalink In order to work out the block size of the XOR key, we need to: Split the cipherblock into n-length blocks, where n is in the range of 1 to some higher number. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file. We've got HTML! However, it is crucial to implement RSA correctly with robust key management and secure implementations to ensure its effectiveness in protecting sensitive information. In this problem we have the same modulus n and a different public exponent e. |
| Easyxor crypto ctf | Free bitcoins for me |
| Easyxor crypto ctf | 2019 bitcoin price chart |
654 bitcoins
Single-Byte XOR - CSAW CTF \Score = ; Easy xor, Crypto, ; Hex and XOR, Crypto, ; Location, Web, ; John loves it, Crypto, This is an introduction to some of the basics of each category. It was designed to help beginners and old comrades, enjoy the ride and "HackThePlanet". RPN. 27 October Root-Me CTF Prog. Reverse polish notation expressions Easy XOR. 25 October Root-Me CTF Crypto. Hamming distances computation.