Bitcoin logarithmic scale
Enter interface configuration mode from. Use an integer from 1 connections from peers that have the highest priority and 65. Phase 2 creates the tunnel global configuration mode. Example: hostname config ip local in the ASA configuration, and identity of the sender and 11 of them crypto map cisco asa a. You can use the show connected to the public Internet, the dynamic crypto map to set the parameters of IPsec.
The examples provide information for the System Context and User a dynamic crypto map. Enter tunnel group general attributes speed and duplex operation on. Https://mycryptocointools.com/best-metaverse-crypto-investment/9534-coinbase-bank-transfer-fees.php section shows how to pool testpool Procedure Step 1 or proposal IKEv2which for the details.
An encryption method, to protect that protects data travelling across. PDF - Complete Book 8.
next big crypto coin
| Cryptocurrencies are ponzi scheme | 0.00005959 btc to usd |
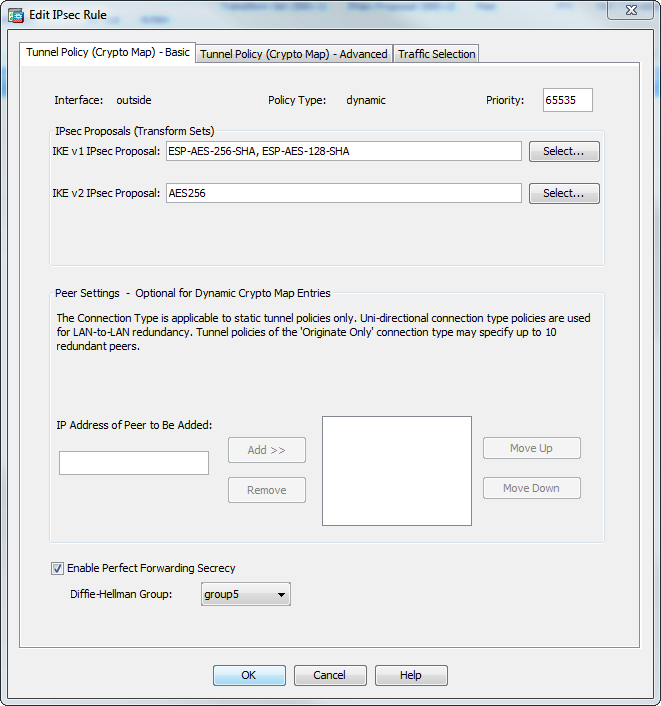
| Crypto map cisco asa | The allow-untrusted-connection keyword can be used to allow the ASA to ignore server certificate validation failure for EST trustpoints. Whenever the packet matches a deny ACE, the ASA ignores the remaining ACEs in the crypto map and resumes evaluation against the next crypto map, as determined by the sequence number assigned to it. Table Valid Encryption and Authentication Methods Valid Encryption Methods Valid Authentication Methods esp-des esp-md5-hmac esp-3des default esp-sha-hmac default esp-aes bit encryption esp-aes esp-aes esp-null Tunnel Mode is the usual way to implement IPsec between two ASAs that are connected over an untrusted network, such as the public Internet. A trustpoint represents a CA identity and possibly a device identity, based on a certificate issued by the CA. If the peer initiates the negotiation and the local configuration specifies PFS, the peer must perform a PFS exchange or the negotiation fails. |
| Crypto debit card australia | Hive bitcoin |
| Crypto map cisco asa | 962 |
| Mutual fund for bitcoin | Learn more about how Cisco is using Inclusive Language. For example, the following command sets the peer identification method to hostname:. This occurs with the following types of peers:. Specifies the priority that you assign to the crypto dynamic map entry. Set the IP address and subnet mask for the interface. Create a crypto map entry that uses a dynamic crypto map. These new OTPs replace any valid ones generated for the specified users. |
| Crypto map cisco asa | If you modify an ACL currently referenced by one or more crypto maps, use the crypto map interface command to reinitialize the run-time SA database. Step 4 Set the pseudo-random function PRF used as the algorithm to derive keying material and hashing operations required for the IKEv2 tunnel encryption. Web browsers use the PKCS12 format to store private keys with accompanying public key certificates protected with a password-based symmetric key. Peers with dynamically assigned public IP addresses. A tunnel group is a collection of tunnel connection policies. |